Introduction
This article describes the method for
- Setting up a Git workflow among multiple repositories across Cloudlab and ALM
- How to keep those repositories in sync
- How to use another repo within a given repo
Developer Workflow
The overall process is as follows:
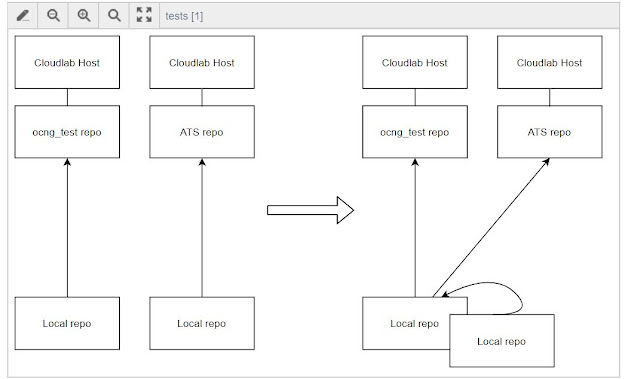
Create a local Git repo that is a clone of Cloudlab
ocng_testrepo.Add the
ocng_testALM repo as a second remote.Fetch all there is in both the repositories.
Checkout the branch you want to work with. Commit your changes.
Merge the changes from origin/development and/or upstream/development into your local development branch. Resolve conflicts, if any.
Push changes to remotes.
Once the branch is pushed to the remote, the usual Git workflow to integrate changes follows, i.e., by creating a merge request for the target branch and triggering reviews.
Keeping Repositories in-sync
The Cloudlab ocng_test repo will periodically pull changes from ALM ocng_repo in master and development branches. Both manual and automated synchronizations are supported through the Cloudlab pipeline. The script to do this is shown below
and illustrated in the below pic.
The merge from development-sync to development branch in Cloudlab ocng_test repo will be manual to account for any merge conflicts.
Using NF Test Cases Repo
The ocng_test repo contains the framework code only. It does not contain the NF specific test cases. The test cases are stored in separate repositories of the NF. If we commit the test cases repository files into Cloudlab instance of ocng_test repo, it will cause problems when merging the changes back to ALM instance of ocng_test repo.
Git provides a few options to use another repo within a given repo.
Git Subtree. Git subtree allows you to insert any repository as a sub-directory of another one. To add PCF
ATSrepo as a subtree inocng_testrepo -The ATS repo will be added as a subdirectory under
ocnftestfolder inocng_testrepo. The main drawback is that pushingocng_testrepo to remote pushes sub-tree's files.Git Submodule. Submodules allow foreign repositories to be embedded within a dedicated subdirectory of the source tree, always pointed at a particular commit. To add PCF
ATSrepo as a submodule inocng_testrepo -The ATS repo will be added as a subdirectory under
ocnftestfolder inocng_testrepo. The advantage over Git subtree is that pushingocng_testrepo to a remote doesn't push sub-module's files. It will, however, create a.gitmodulesfile under root folder with following content -As a Subdirectory. Another option is to put
ATSrepo as a subdirectory in theocng_testlocal repo. Add the subfolder to .gitignore in your main repo.The ATS repo will be added as a subdirectory under
ocnftestfolder inocng_testrepo. Addocnftest/ocpcf/*in.gitignoreto avoid the contents ofocpcfdirectory to be pushed to theocng_testremote.


Comments
Post a Comment